There are two kinds of enterprises in today’s world: the ones that know they’ve been hacked, and the ones that don’t know they’ve been hacked. To make matters worse, hackers are getting better and better at hiding their tracks. Companies often don’t discover breaches until months later, long after the criminals have absconded with vital corporate data.
The clamor surrounding enterprise cybersecurity is to be expected, of course, with all the breaches over the last year or so. Home Depot. Target. Anthem. The list goes on and on. And with breaches come enterprise dollars, frantically swirling over the proverbial barn door after the horse is long gone.
Perimeter-based security approaches (namely, relying upon firewalls) have proven themselves to be woefully inadequate. Through hard-won experience we’ve learned that every network is untrusted.
Furthermore, once hackers penetrate a corporate network, they typically sneak around from place to place, seeking further vulnerabilities until they happen upon their goal, which is typically data they’d like to steal.
Network segmentation is an important technique for limiting the damage such a wandering cybercriminal might cause. Compartmentalize the network into different segments, so the reasoning goes, and attackers will have a more difficult time moving around the network.
The problem with most approaches to network segmentation, however, is that companies end up with a hodgepodge of different technologies – SSL and TLS security, IPsec tunneling, VLANs, ACLs, FW DMZs, Internet WAN DMZs, routing policies and application-layer encryption controls, to name a few.
However, this alphabet soup of traditional network segmentation approaches are all tied to network infrastructure, rather than business rules and policies. They are infrastructure-centric rather than business-centric.
As a result, they are inflexible and expensive to manage. Worst of all, the sheer complexity of such a mishmash of technologies increases the risk of a misconfiguration – thus opening yet another door for a wily hacker.
Pittsburgh, PA-based Certes Networks aims to slow down this behavior by leveraging sophisticated encryption to compartmentalize the network. Its technology creates different segments for each business application (email, CRM, source control, payroll, etc.) independent of the network infrastructure, and each application segment has its own cryptographic keys. This segmentation prevents hackers from moving easily in a lateral fashion from application to application.
Such business-centric segmentation that protects application traffic with strong cryptography, granting access to each application based upon user roles is known as crypto-segmentation.
Crypto-segmentation establishes role-based access to cryptographically isolated, networked applications. Instead of the physical network segments that constitute the infrastructure-centric approach to segmentation, crypto-segmentation establishes logical, policy-driven application segmentation that abstracts the physical elements of the infrastructure.
In essence, the organization encrypts each virtual segment separately with a unique key. Security admins base the definition of each crypto-segment upon business rules for each application, where user roles and business policies determine access rights that depend on verified identity.
The robustness of crypto-segmentation, therefore, centers on key management rather than a hodgepodge of separate tools and network infrastructure components. Security admins maintain complete control of the keys and the key lifecycle. And because organizations can’t fully trust their admins, crypto-segmentation also requires centralized audit logging for all access to the policies.
The result: when breaches occur (and they will), the compromise of networks, applications, or even users does not compromise other crypto-segments on the network.
Crypto-segmentation, in essence, compartmentalizes the network, preventing the lateral movement that was the hallmark of most of the significant breaches over last two years.
Certes Networks’ CryptoFlow Solution
Certes Networks’ core offering is the CryptoFlow Solution, which uses software-defined crypto-segmentation to safeguard enterprise applications over any network for any user, on any device.
A CryptoFlow is a secure virtual overlay for each application, protecting each application with strong encryption, with its own security profile and keys. It extends to wherever the application resides in either physical or virtual data centers or private or public clouds – wherever users want access, across any network, to any of their chosen devices.
CryptoFlows also provide a single point of control for end-to-end protection of sensitive applications. Via this crypto-segmentation, CryptoFlows isolate and protect sensitive applications from the application server to users’ end-point devices, regardless of their location. Furthermore, CryptoFlows auto-generate session keys and protect them from any user, even one with administrative privileges.
As a result, IT security managers have a single point of control where they can automatically crypto-segment application flows across networks, clouds, and data centers inside or outside the enterprise, granting access to CryptoFlows based upon a user’s role.
Even if hackers breach the firewall, they cannot access sensitive applications, because they are not an authorized user of that CryptoFlow. Furthermore, even if hackers compromise a contractor or member of the supply chain, the attacker can only get access to the CryptoFlow that the contractor was authorized for, like a billing or inventory management application. All other applications are safe on their own CryptoFlows, blocking lateral movement or hopping from application to application.
In addition, Certes offers CryptoFlows that create protected network segments that extend beyond the enterprise perimeter, including CryptoFlow Cloud, CryptoFlow WAN, CryptoFlow Mobile, and CryptoFlow B2B. The diagram below illustrates the relationships among these products.
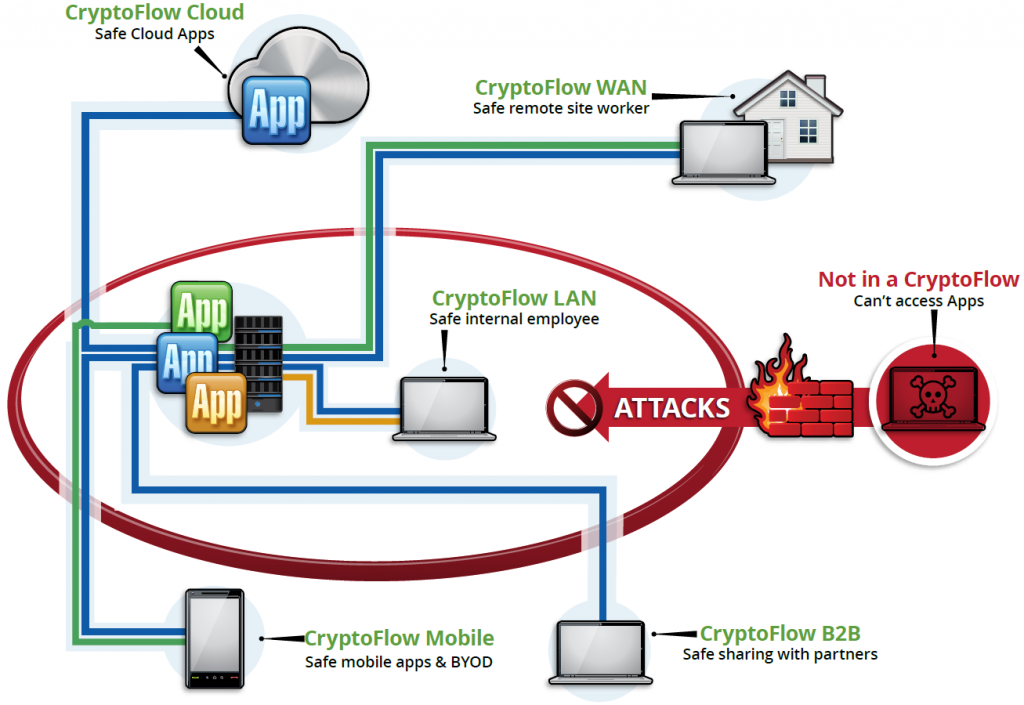 Certes Networks’ CryptoFlow Products (source: Certes Networks)
Certes Networks’ CryptoFlow Products (source: Certes Networks)
Each of the products above resemble a standard virtual private network (VPN), in that they each create a secure virtual overlay over the physical Internet in order to establish a cryptographically secure application segment.
The difference is the way that Certes provides consistent business controls for the policies across such a diverse network. CryptoFlows can secure the most complex of distributed networks in a seamless, easy to manage manner.
The Intellyx Take
No security tool can prevent or mitigate all cyberattacks completely, and Certes Networks’ CryptoFlow Solution is no exception. Any compartmentalization approach might still allow a hacker to do damage or steal data within a single segment.
However, Certes unquestionably raises the difficulty level for attackers. Even if they were able to compromise a single segment, they wouldn’t be able to access any of the encrypted data without either cracking the encryption or stealing the private key.
Because Certes uses the latest encryption methodologies, any brute force attack would be prohibitively expensive. Stealing a private key, furthermore, would require an insider to cooperate with the attackers.
However, Certes even mitigates the “insider with administrative privileges” weakness (in other words, the Edward Snowden scenario) via autogenerated keys and centralized audit logging for all access to the policies – and even the admins cannot turn the audit logging off.
In reality, however, exploring such an improbable threat surface is largely an academic exercise, as the real question centers on deterrence. Since breaking into CryptoFlows in order to steal valuable data is so extraordinarily difficult, cybercriminals will simply select easier targets – even for unusually valuable data.
Cybersecurity, in the final analysis, is a battle of wits. Attacks are constant. We can take breaches for granted. So for many enterprises, mitigating the damage and discouraging further attacks is the final line in the sand. Crypto-segmentation draws that line.
Click here to download the Intellyx white paper Securing the Frictionless Enterprise, or register for the corresponding webinar on September 24, 2015, at 11:00 EDT.
Certes Networks is an Intellyx customer. Intellyx retains final editorial control of this article.




Comments