By Jason Bloomberg
This is a true story. The targeted company wishes to remain anonymous – typical in instances of compromise – so we’ll call it Horizon.
With the help of a team of experts, Horizon was able to stop a determined attacker in its tracks. Here’s how they did it.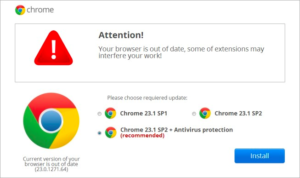
The Vulnerability
Horizon had signed up for the Managed Detection and Response (MDR) service from Open Systems – a fortuitous choice, as this story will show.
Unfortunately, Horizon’s deployment of Open Systems’ SD-WAN technology was not complete at the time of the attack. The company was in the process of rolling out Open Systems Network Detection and Response (NDR) technology, including SD-WAN, firewalls and secure web gateways, but the attacker found an entry point not yet protected by this technology.
The attack vector: a simple phishing attack, using a fake Google Chrome download alert (see the diagram below). The attacker cast a wide net with its social engineering, knowing that a single click on the alert’s install button would give the attacker entry to Horizon’s network.



