At last week’s Think 2019 conference, IBM made a splash with its announcement that its Watson AI platform would run on the Amazon AWS, Microsoft…
Distributed denial of service (DDoS) attacks are a particularly pernicious form of cyberattack where the bad actor seeks to take down a web site or…
In 2002, I wrote an article entitled Web Services Idées Fortes — idées fortes meaning powerful ideas. The three powerful ideas: asynchrony, loose coupling, and…
By Charles Araujo Creating a breakout customer experience is not about technology, but there is also no question that it is often the little technical…
By Jason English The overture to business reality is ending for SD-WAN solutions. Now a company’s entire network, security and software operating environment is deployed in…
In the early days of cloud computing, private clouds promised the scalability, elasticity, and manageability of public clouds combined with the security and control over…
“‘Cloud native’ is more than ‘cloud only,’” I wrote in my December 2017 article Seven Remarkable Takeaways From Massive Kubernetes Conference. “It means bringing cloud-centric…
For many years, legacy modernization was a black or white affair: either rip out all the old technology and start afresh or make do with…
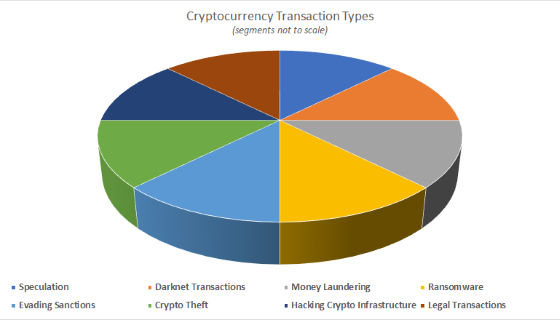
Even now that the Bitcoin bubble has long since popped, increasingly desperate cryptocurrency (crypto) fans are still exhorting the virtues of the technology’s supposedly rosy…
In a recent article, I took a critical look at the burgeoning robotic process automation (RPA) market – and found that in many cases, vendor…