Podcast / vCast for October 19, 2020: JE and Scott King (@thescottking), mobile app cybersecurity evangelist from Zimperium, discuss how current post-Covid events and an…
An Intellyx Brain Candy Brief Lastline leverages AI, machine learning (ML) in particular, to identify malicious behavior on networks, both on premises and in the…
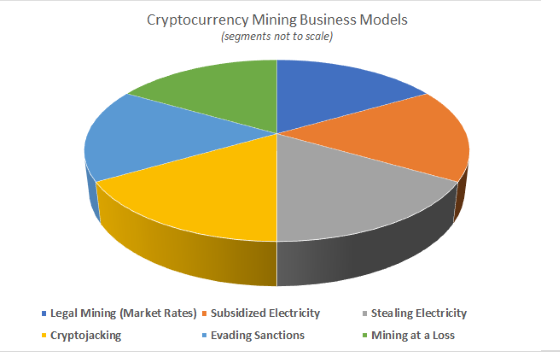
Savvy readers of yesterday’s article, The Eight Most Popular Cryptocurrency Transaction Types Are Not What You Expect, may have noticed an important omission: any discussion…
An Intellyx Brain Candy Brief As software vendors get wise to popular cybersecurity attacks, they harden their offerings, pushing the attackers to come up with…
When you buy a high-tech device like an iPhone, you realize much of the value is in the software, and you expect to agree to…
An Intellyx Brain Candy Brief At some point, all malware must take some action that is outside the norm for well-behaving software. Perhaps it attempts…
The battle lines are clear: the FBI is using the courts to try to force Apple to write malware that will provide a backdoor into…
Cybercriminals that mount ransomware attacks, where malware holds victims’ files or entire computers hostage until they pay a ransom, are increasingly targeting businesses, according to…