An Intellyx BrainBlog, for Bridgecrew
Supply chain seems to be on the tip of everyone’s tongue these days.
We’re experiencing massive volatility in global supply chains, the multiparty networks that produce the commodities and manufactured products every society depends upon. Inconsistent supplies of raw materials and parts, logistical nightmares, and constrained industrial capacity are interrupting practically everything. Customers and businesses are bearing the brunt of inventory shortages and higher prices.
Just like the physical supply chains of factories, container ships, and trains behind the delivery of goods to customers, there is a parallel software supply chain (or SSC) to deliver cloud-native applications. Most companies didn’t worry enough about the SSC until the recent Solarwinds hack pointed out just how vulnerable our software can be throughout its lifecycle.
Although it was certainly not the first software supply chain attack, the world sat up and took notice because of the breadth and depth of this attack. And this problem isn’t going away anytime soon. The European Union predicted a 4X increase in SSC attacks in 2020, and analysts predict that nearly half of all companies will experience such an exploit by the year 2025. So what can be done to prevent it?
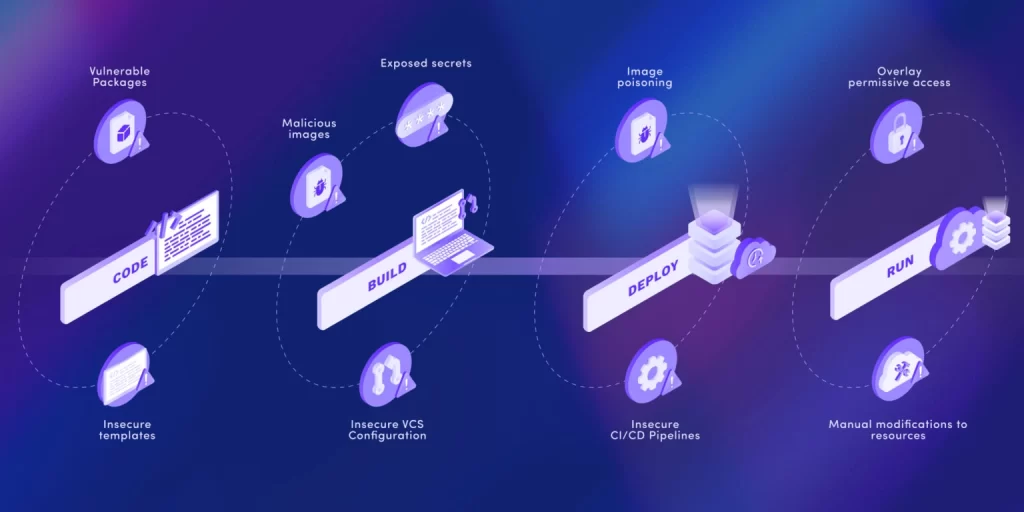
Every layer that comprises a cloud-native application, from root-level operating systems, to application code and the repositories it’s stored in, to the access and control planes used to manage a cloud-hosted application estate, has potential weaknesses that introduce risk within a highly interconnected software supply chain.
What comprises the software supply chain?
Much like the many parts and suppliers that contribute to physical supply chains, software supply chains are made up of the combination of several platforms and components – each of which arrived through their own open-source or commercial production pipelines.
- Version control systems (VCS) such as GitHub, GitLab, or Bitbucket can govern multiple project repositories to store and manage all of the assets within a given company’s SSC. Unfettered access to these systems can not only allow exploits to enter company systems at a code level, but it can also result in a loss of intellectual property and operational integrity.
- Infrastructure as code (or IaC) tools such as Terraform, CloudFormation, Chef or Puppet scripts, Kubernetes manifests or Helm charts provide the instructions for configuring all elements of an application’s infrastructure. Misconfigurations of IaC can get persisted again and again across deployments …